
1984 Has Been Brought To You By The Fine Folks At AT&T!
BY ELLEN NAKASHIMA WASHINGTON POST STAFF WRITER His first inkling that something was amiss came in summer 2002 when he opened the door to admit a visitor from the National Security Agency to an office of AT&T in San Francisco.”What the heck is the NSA doing here?” Mark Klein, a former AT&T technician, said he asked himself.
A year or so later, he stumbled upon documents that, he said, nearly caused him to fall out of his chair. The documents, he said, show that the NSA gained access to massive amounts of e-mail and search and other Internet records of more than a dozen global and regional telecommunications providers. AT&T allowed the agency to hook into its network at a facility in San Francisco and, according to Klein, many
of the other telecom companies probably knew nothing about it.Klein is in Washington this week to share his story in the hope that it will persuade lawmakers not to grant legal immunity to telecommunications firms that helped the government in its anti-terrorism efforts.
The plain-spoken, bespectacled Klein, 62, said he may be the only person in the country in a position to discuss firsthand knowledge of an important aspect of the Bush administration’s domestic surveillance program. He is retired, so he isn’t worried about losing his job. He did not have security clearance, and the documents in his possession were not classified, he said. He has no qualms about “turning in,” as he put it, the company where he worked for 22 years until he retired in 2004.
“If they’ve done something massively illegal and unconstitutional — well, they should suffer the consequences,” Klein said. “It’s not my place to feel bad for them. They made their bed, they have to lie in it. The ones who did [anything wrong], you can be sure, are high up in the company. Not the average Joes, who I enjoyed working with.”
In an interview yesterday, he alleged that the NSA set up a system that vacuumed up Internet and phone-call data from ordinary Americans with the cooperation of AT&T. Contrary to the government’s depiction of its surveillance program as aimed at overseas terrorists, Klein said, much of the data sent through AT&T to the NSA was purely domestic. Klein said he believes that the NSA was analyzing the records for usage patterns as well as for content.
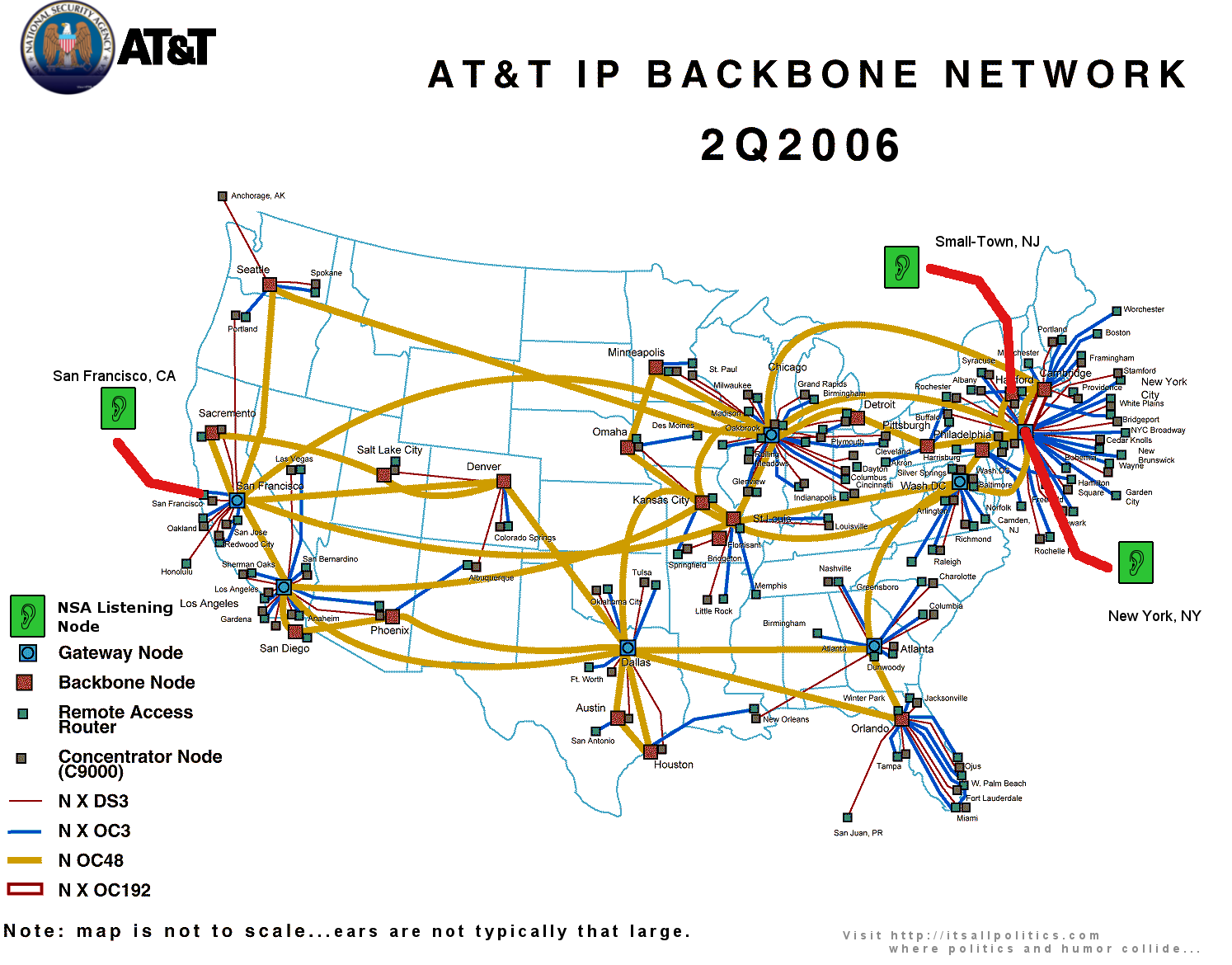
He said the NSA built a special room to receive data streamed through an AT&T Internet room containing “peering links,” or major connections to other telecom providers. The largest of the links delivered 2.5 gigabits of data — the equivalent of one-quarter of the Encyclopedia Britannica‘s text — per second, said Klein, whose documents and eyewitness account form the basis of one of the first lawsuits filed against the telecom giants after the government’s warrantless-surveillance program was reported in the New York Times in December 2005. MORE
The following is a summary from WIRED of the expert testimony of J. Scott Marcus, a former FCC advisor and holder of Top Secret security clearances. Mr. Marcus was hired by Electronic Frontier Foundation to assess the accuracy and validity of their lawsuit against AT&T. The judge in the case has only allowed parts of his testimony to be released to the public.
An internet pioneer and former FCC advisor who held a Top Secret security clearance, Marcus applies a Sherlock Holmes level of reasoning to his dissection of the evidence in the case: 120-pages of AT&T manuals that EFF filed under seal, and whistleblower Mark Klein’s observations inside the company’s San Francisco switching center:
- The AT&T documents are authentic. That AT&T insists they remain under seal is evidence enough of this, but Marcus points out that the writing style is pure Bell System, with the “meticulous attention to detail that is typical of AT&T operations.”
- There may be dozens of surveillance rooms in AT&T offices around the country. Among other things, Marcus finds that portions of the documents are written to cover a number of different equipment rack configurations, “consistent with a deployment to 15 to 20” secret rooms.
- The internet surveillance program covers domestic traffic, not just international traffic. Marcus notes that the AT&T spy rooms are “in far more locations than would be required to catch the majority of international traffic”; the configuration in the San Francisco office promiscuously sends all data into the secret room; and there’s no reliable way an analysis could infer a user’s physical location from their IP address. This, of course, directly contradicts President Bush’s description of the “Terrorist Surveillance Program.”
- The system is capable of looking at content, not just addresses. The configuration described in the Klein documents — presumably the Narus software in particular — “exists primarily to conduct sophisticated rule-based analysis of content”, Marcus concludes.
Perhaps the most interesting — and, in retrospect, obvious — point Marcus makes is that AT&T customers aren’t the only ones apparently being tapped. “Transit” traffic originating with one ISP and destined for another is also being sniffed if it crosses AT&T’s network. Ironically, because the taps are installed at the point at which that network connects to the rest of the world, the safest web surfers are AT&T subscribers visiting websites hosted on AT&T’s network. Their traffic doesn’t pass through the splitters.
Find out how to detect if your Internet traffic is being diverted to the NSA after the jump…
With that in mind, here’s the 27B Stroke 6 guide to detecting if your traffic is being funneled into the secret room on San Francisco’s Folsom street.
If you’re a Windows user, fire up an MS-DOS command prompt. Now type tracert followed by the domain name of the website, e-mail host, VoIP switch, or whatever destination you’re interested in. Watch as the program spits out your route, line by line.
C:\> tracert nsa.gov
1 2 ms 2 ms 2 ms 12.110.110.204
[...]
7 11 ms 14 ms 10 ms as-0-0.bbr2.SanJose1.Level3.net [64.159.0.218]
8 13 12 19 ms ae-23-56.car3.SanJose1.Level3.net [4.68.123.173]
9 18 ms 16 ms 16 ms 192.205.33.17
10 88 ms 92 ms 91 ms tbr2-p012201.sffca.ip.att.net [12.123.13.186]
11 88 ms 90 ms 88 ms tbr1-cl2.sl9mo.ip.att.net [12.122.10.41]
12 89 ms 97 ms 89 ms tbr1-cl4.wswdc.ip.att.net [12.122.10.29]
13 89 ms 88 ms 88 ms ar2-a3120s6.wswdc.ip.att.net [12.123.8.65]
14 102 ms 93 ms 112 ms 12.127.209.214
15 94 ms 94 ms 93 ms 12.110.110.13
16 * * *
17 * * *
18 * *
In the above example, my traffic is jumping from Level 3 Communications to AT&T’s network in San Francisco, presumably over the OC-48 circuit that AT&T tapped on February 20th, 2003, according to the Klein docs.The magic string you’re looking for is sffca.ip.att.net. If it’s present immediately above or below a non-att.net entry, then — by Klein’s allegations — your packets are being copied into room 641A, and from there, illegally, to the NSA.
Of course, if Marcus is correct and AT&T has installed these secret rooms all around the country, then any att.net entry in your route is a bad sign.
RELATED: How To Stop The Spying On Americans

